Ecosystem Architecture
Publication Date: 25.05.2019
Note: For the use of Developer Assets, these Terms and Conditions apply. Please also read the Requirements Notation and Conventions.
1. Introduction
This document gives an architectural overview of the ecosystem. It is relevant for all parties who are interested in and like to understand the basic concepts, the involved parties and their interplay. Readers may be solution architects or software developers who are in charge of implementing services that are supposed to participate in the ecosystem. Such a service may act in one of the following roles: Identity Provider (IDP), Service Provider (SP) or Relying Party (RP) such as online shops, telecom or insurance companies.
The document focuses on base concepts of and the operational and technical interfaces which have to be invoked or provided by partners who like to become part of . The document describes the concept of the ecosystem. Additional documents provide more information on specific aspects of .
1.1. References
|
Defines the technical requirements an IDP must fulfill to become part of the ecosystem. |
|
|
Documentation of the APIs to integrate IDPs and SPs with the platform for the purpose of credential management and billing mediation. |
|
|
This guide is dedicated towards RP developers and describes the steps to be taken in order to integrate a RP with . |
2. Overview
introduces a scheme that enables bank customers to use their online banking accounts for conducting various digital transactions, such as login, registration, identification, payment and signing, with web sites or apps (in general named Relying Parties or RPs) and service providers (SP) that provide enhanced services to RPs via APIs.
The user’s bank ideally acts as her core Service Provider (designated as IDP). These ‚Active banks‘ continue to hold the user’s personal and bank data. Active banks keep the interface to the customer, the RP, and other SPs and provide an IDP implementation according to the free IDP Specification. These banks can generate revenue by exposing APIs and sharing user and account data with RPs and SPs if requested and approved by the respective user.
Passive banks don’t have a contractual relationship with and do not provide an IDP for their customer. However will be available to customers of these banks through TPPs that provide IDPs for passive bank in the scheme. These IDPs use the respective bank’s public interfaces (such as their PSD2 Access to Account API). Passive banks thus form a part of the scheme without their cooperation. Any passive bank may take over the IDP role for their customers if it becomes an active bank.
In both scenarios RPs and SPs can obtain all PSD2 services (account holder, IBAN, 90 days of transaction history, SEPA transfer and mandates) as well as user email and postal address free of charge. Active banks, passive bank IDPs, and other Service Providers can provide additional data for free or at a premium.
Users of both active and passive banks don’t have a user account. instead leverages the existing online banking account by orchestrating a network of IDPs, which provide a federated ID to RPs[1]. Data is never transferred to an RP without a prior user consent and never transferred to the scheme itself.
Third party party Service Providers will enrich the ecosystem by providing additional services, like enhanced scores or electronic signatures based on the bank-provided authentication capabilities and verified data.
USER PERSPECTIVE: allows me to use my online banking credentials to login to third party websites and apps and to use my bank data for services that require a high level of trust and authenticity. It enables me to initiate SEPA transfers directly at my bank and prove my verified identity to access services that would otherwise require a separate, more cumbersome verification method, e.g., video ID or a physical processes.
RP PERSPECTIVE: enables me to easily authenticate and identify users with their banking account without the need to integrate all banks separately with my service. I get all PSD2 services for free, through a single API Specification and without needing to be certified as Account Information Service Provider (AISP) or Payment Initiation Service Provider (PISP). The same API Specification allows me to access bank-verified identity and account data. Moreover, I can use further -standardized or third party party services, e.g., to enrich the user’s data or to let my users sign contracts with qualified electronic signatures.
ACTIVE BANK PERSPECTIVE: is an ecosystem where I keep the customer interface and the ability to authenticate my users directly[2], transfer data directly to RPs without the need for third party aggregators, and become the digital master key for my customers.
I can monetize my verified customer and account data by making it accessible to all RPs and SPs in the scheme in compliance with GDPR and PSD2 using open standards and a well-defined commercial and legal framework provided by .
SP PERSPECTIVE: is a marketplace where I can offer my services that are based on verified user identities, data and account data. I can reach a wide range of Relying Parties and other Service Providers and use as billing partner for my offering.
PERSPECTIVE: The platform facilitates the scheme by managing the trust relationships among IDPs, SPs and RPs. The Account Chooser connects RPs and IDPs (and SPs) on behalf of the user. The user determines the bank she wants to use with and this decision is retained in order to provide SSO in subsequent transactions even if a strict 3rd party cookie policy is in place. can be used by IDPs and SPs as a billing and clearing platform.
To become a part of the scheme, partners have to sign up with a RP agent. Banks, RPs and SPs get access to all relevant information and technical specification that are relevant to become part of the ecosystem at https://docs.verimi.de/openbanking/docs.
After successfully implementing the required interfaces and testing of the end-to-end system behavior in the sandbox, will activate the partner for the live environment.
3. Overall Architecture
This diagram illustrates the overall architecture of the scheme. It shows the involved parties and their relationships.
A Relying Party (RP) represents a site or app
wanting to integrate services into its overall proposition,
e.g. to identify the user according to anti money laundering
law.
The IDP plays the most fundamental role from the
user’s perspective. There is an individual IDP for every bank
in the scheme, which provides the functionality for the
respective user base with the bank’s look and feel. The IDP
authenticates the user taking full advantage of existing
methods (such as online banking credentials or mobile apps
capable of receiving push notifications and using biometric
authentication) and gathers the user’s consent for any
transaction.
| All data exchange and service access happens directly between RP and IDP. is not involved in these flows. |
This also means that the RP always first needs to determine the IDP to talk to on behalf of a certain user.
The Account Chooser is used for that purpose. The
user identifies her bank at the account chooser’s user
interface and the account chooser in turn identifies the
respective IDP and its so-called service configuration, which
contains the configuration data and URLs required for the RP
to use the various services provided for the customers of the
respective bank.
| The IDP may provide those services itself or delegate this to other services providers that either act on behalf of the IDP or independently. |
From the perspective of a RP, Account Chooser, Service Configuration and the set of all IDPs are form a “Virtual IDP”.
The platform provides components and interfaces
to orchestrate the OpenID Connect/OAuth based flows and use of
further APIs between users, RPs, SPs, and IDPs.
The platform provides directories that enable the partners to know each other and to query all relevant details to setup a secure and trustable authentication for any user, independent of which RP she is supposed to use and which IDP is the one she has an account for. The platform also provides a service to collect billing data to facilitate invoicing and settlement among the involved parties.
For a detailed explanation of the platform please consult the Platform Documentation.
Third party Service Providers may offer their
services to RPs in the scheme. These SPs can rely on trusted
access tokens issued by the IDPs containing bank approved
identity information and user data to fulfill services which
require a high level of assurance. Service Providers may
utilize other services provided by the IDP or other service
providers to implement their service.
Most scheme partners, IDPs, SPs and RPs, are onboarded through
so-called Agents. These are business partners
acquiring the aforementioned partners through their network,
perform the KYC check, close the contract and provide with the
information needed to set up the respective technical
accounts. We will also serve as agent for partners that want
to interact directly with .
| The use of the the button, the specifications, and the platform is and will remain free for all parties using the scheme. |
4. Base concepts
uses the open standard OAuth 2.0 to authorize access to any kind of service in the scheme. Every IDP is a OAuth Authorization Server that utilizes online banking credentials to authenticate users, gather their consent for service access and user data transfer, and issues access tokens that RPs and SPs use to authorize service access. On top of OAuth, the open standard OpenID Connect is used to provide identity service to RPs.
The scheme forms a virtual IDP composed of thousands of independent IDPs. This poses the following challenges:
HOW IS THE VIRTUAL IDP EXPOSED TO RPs? From an architectural perspective, one could build a proxy encapsulating all IDPs from the RP. Although this sounds beneficial (esp. from an RPs perspective) on first sight, it poses significant technical, legal, and privacy issues since user data would flow through systems. To assess the impact, one needs to take into account that is designed to become an international ecosystem spanning different jurisdictions. This is why is designed as a scheme of independent IDPs[3], where every IDP directly interacts with the respective RP. ensures interoperability of all IDPs towards RPs by defining standard APIs every IDP in the scheme must comply with (see IDP Specification).
The scheme approach (which is distributed in nature) creates the next challenge:
IS IT POSSIBLE FOR A RP TO USE ALL IDPs OF THE SCHEME WITH A SINGLE CREDENTIAL? This is enabled by maintaining a universal client id for every RP, which is applicable at any IDP. RPs use public key cryptography to authenticate with IDPs, where manages the RP’s public key certificates or URLs pointing to public key certificates. IDPs obtain all RP data (e.g. name, client_id, certificates, redirect URIs, allowed scopes and claims, tos & policy URLs) from the RP directory and maintain it locally for use during the OAuth (OpenID Connect) Flow. IDPs are supposed to periodically synchronize with the RP directory.
As a result, an RP can interact with any IDP without knowing
it beforehand. The RP uses its universal
client_id and the service configuration of a
particular IDP to establish the connection at runtime and at
the user’s request.
| Due to security, legal, and commercial requirements, currently only supports confidential clients (see RFC 6749, section 2.1). |
HOW DOES AN RP DETERMINE WHETHER AN IDP REALLY BELONGS TO ? The account chooser and the service configuration service are the trusted sources of IDP data. The identity provider ensures authenticity and integrity of this data. RP MUST NOT use any endpoint URL obtained anywhere else.
is designed to manage a large number of partners in a highly scalable, uniform and comprehensive way. To fulfil this comprehensive approach of an ecosystem with multiple 3rd party systems but a uniform system behavior, all parties have to follow the same integration guidelines and provide or invoke consistent interfaces. Even though well known standards are used to become part of the ecosystem, will define profiles, details, extensions and interpretations of all used protocols and standards if needed by way of the IDP Specification. It profiles OAuth and OpenID Connect in order to make it fit the requirements and objectives. It also defines the APIs for accessing account information, initiate payment and remotely create electronic signatures in the scheme.
5. Service Architecture
On an overall architectural level, every IDP provides all services for the customers of the respective bank. However, it is vital for that functions provided by fintechs and large techs are also available in the user ecosystem. Because is a federated System comprised of thousands of banks it is difficult to ensure all banks offer all services from the beginning. This is why it is critical that service providers can fill the gaps by offering services like Qualified Electronic Signatures (QES) or scores on top of the banks’ capabilities.
This section defines the service architecture required to build and grow such an ecosystem. It defines how the services offered to the customers of a certain bank (the IDP) are provided and how those services interdepend.
This section defines a set of core services that every bank shall implement and offer to both RPs and SP. It also discusses further value added services that either the bank or another service provider can implement and offer to the customers of the respective bank.
5.1. Service Architecture Overview
The following figure shows the Service Architecture.

The innermost circle consists of the base functionality of a IDP required to enable any services. Those functions consist of user management, including management of multi-factor credentials, the integration with the platform for the purpose of synchronizing RP and SP data and sending billing related data to , and the base functionality needed to authorize access to arbitrary APIs based on bank identities.
The next layer consists of base services that can be used directly by RPs or by SPs to in turn provide value added services to RPs (or other SPs). Those services are:
-
Identity: the capability to provide verified and unverified identity & bank data and to authenticate users with single or two factor authentication.
-
Account Information: the capability to provide account data including balance and transaction history
-
Payment Initiation: the capability to initiate a SEPA credit transfer
| Access authorization for those APIs is provided by the base functionality API Authorization, which enables an integrated authorization process across the different APIs. This allows an RP to acquire access authorization for multiple APIs in a single authorization transaction providing the best possible user experience. |
Base functionality and services together comprise the Core Services any IDP MUST implement and provide to RPs and SPs.
The outer ring consists of examples of value added services that can be provided by the IDP or by another service provider.
-
Electronic Signature: a (Q)TSP can provide electronic signatures based on the identity data and API authorization provided by the IDP.
-
AML ID: a service for identity verification according to the (German) Anti Money Laundering Law can be built based on the identity services, the ability to initiate payments and API authorization (all) provided by the IDP.
-
Credit: a credit service can utilize account information as provided by the IDP to calculate risk and score.
-
Scoring: various scores can be calculated based on the account information provided by the IDP and other sources.
-
Account Information Analysis: there are already services in the market determining information from account information, such services can be integrated into the scheme and utilize both the account information and the API authorization provided by the IDP.
The clear definition of core services shall allow arbitrary service providers to build value added services on top of core IDP capabilities across all IDPs. If an IDP decides to provide such a value added service for its customers (only), it can also use proprietary APIs and services.
We recommend that banks offer as many services as possible themselves as this cements the bank’s role and reduces the data shared with third parties. If a bank analyzes Account data and provides derived information such as the name of the employer directly to the wrap there is no need for an SP to be involved and receive this data as well.
If a bank cannot provide a Value Added Service, we recommend that the bank outsources the service to a company (based on a data processing agreement).
| Although already defined some value added services, the vision is that service providers increase the number of services (and thus the attractiveness of the ecosystem) by (independently) inventing and providing services in the ecosystem (in the same way as apps contribute to the attractiveness of the iOS or Android ecosystem). |
5.2. Core Services
This section gives a more detailed description of the core services.
5.2.1. User Management
The IDP must maintain user accounts with stable user ids to allow recognition of users and association of further user-specific data in the IDP and with RPs and SPs.
The IDP must maintain two independent authentication factors for every user account incl. recovery processes.
Further requirements: * authentication factors from different authentication factor categories (knowledge, possession, inheritance) * at least one factor utilizing dynamic authentication (typically possession) * 1st factor must be Online-Banking login, second factor should be user’s preferred Online Banking SCA method
The IDP must recognize returning users and simplify their authentication process if possible, e.g., by utilizing SSO or step-up authentication.
5.2.2. API Authorization
API authorization is implemented using OAuth 2.0.
Every IDP is an OAuth Authorization Server (AS). It allows clients (Relying Parties) to obtain the authorization to access services advertised in the scheme on behalf of the particular bank customer.
Such services may be provided by the respective bank itself (such as identity providing or payment initiation) or by other parties. All APIs provided in the context of a certain bank use the same bank-provided AS for user authentication and access authorization. This allows for single-sign-on experience across authorization requests and it also allows to combine requests for access to different resources in a single transaction. As an example, a client could request access to identity data (OpenID Connect) and account information (AIS) in a single OAuth authorization request just by combining the respective scope values. This will result in a competitive user experience and give clients maximum flexibility in designing their user flow.
| SPs may also access other services on behalf of the user. The AS supports this use case by gathering the consent on behalf of such a service and allowing the service to exchange access tokens presented by a client into access tokens the service itself can use for service requests. |
The Authorization Server leverages the existing online banking user base and underlying strong identities to the services in the scheme. The Authorization Server uses the existing Online Banking Credentials to authenticate users, thus allowing bank customers to use -based services without the need to set up new credentials. The aim is to achieve a superior user experience and high conversion rates at the service providers.
Before a client can access a service on behalf of the user, the Authorization Server will always request the user’s consent. If the user denies the inquiry, access won’t be granted. If access is granted, the client is provided with an access token representing its permissions and carrying or referring to the user and account data needed to fulfill the particular service.
5.2.3. Platform Integration
RP settings and credentials are managed centrally by the platform. IDPs must query the respective data from the RP directory periodically, store this RP data locally.
SP settings are managed centrally by the platform. ASs MUST query the respective data from the SP directory periodically, store this SP data locally.
Every IDP must send information about services delivered to RPs or SPs to the platform’s mediation service in order to enable settlement and billing.
The platform API documentation can be found at https://docs.sandbox.openbanking.verimi.cloud/.
5.3. Identity Service
The IDP must manage user identification and user accounts including verified person data in accordance with German Anti Money Laundering Law or eIDAS trust level “substantial”.
RPs use the service via an interface based on OpenID Connect. The OpenID Connect functionality is implemented as an extension of the OAuth AS, i.e. they share the same authorization and token endpoint. This allows for combined OAuth/OpenID requests, e.g. to ask for the user data and the permission for a SEPA credit transfer by combining the respective scope values.
SPs are provided with identity data via the OAuth Token Introspection Endpoint.
More details can be found in the IDP Specification.
5.4. Account Information Service
The Account Information API is a profile of Berlin Group’s NextGenPSD2 XS2A Framework. This profile combines (a reduced feature set of) Berlin Group’s account information service with the client management framework.
This service allows RPs and SPs to access account information, such as a list of accounts, transactions and account balance with the consent of the user. User authentication and authorization of all AIS transactions is performed by the AS of the respective bank.
More details can be found in the Account Information Service Specification.
5.5. Payment Initiation Service
The payment initiation API is a profile of Berlin Group’s NextGenPSD2 XS2A Framework. This profile combines the framework for credential and trust management with Berlin Group’s payment initiation API (OAuth SCA Approach) while using a reduced feature & parameter set.
The Payment Initiation Service as defined in this document provides clients with a capability to initiate SEPA credit transfers. User authentication and authorization of all PIS transactions is performed by the AS of the respective bank.
More details can be found in the Payment Initiation Service Specification.
5.6. Value Added Service Composition
This section describes the way value added services are built by utilizing or composing core services.
5.6.1. Example: Qualified Electronic Signature
Prerequisites
An QTSP offers an API for remote signature creation in the ecosystem. This QTSP is the SP in the following.
The scope to request authorization for this API and the corresponding lodging intent resource scheme are known to RPs and IDPs. The SP configuration in the platform contains a definition of the requested user and consent data as well as the authentication requirements of the QTSP.
Signing Flow
An RP wants to use the signing service. It first determines the IDP and QTSP (SP) to talk to using the account chooser and service configuration.
The RP then creates a lodging intent resource containing the parameters for the intended signing transaction with the IDP and initiates an authorization process with the IDP using the scope value identifying the lodging intent resource.
Based on scope value and accompanying lodging intent data, the IDP determines the SP’s identity along with the required user and consent data and the desired authentication policy (1FA or 2FA).
The IDP will authenticate the user according to the SP’s policy.
The IDP will then ask the user to * allow the RP to use the QTSP API to create a signature on behalf of the user * asks the user for the approval to share the user data as requested by the SP with the SP * asks the user to consent to further documents the SP requires the user to consent to (e.g. terms of service)
If the authorization process succeeded, the IDP provides the RP with an access token.
The RP uses the access token to call the signing API of the QTSP.
The QTSP receives the request including this access token and uses the IDP’s OAuth Token Introspection Endpoint to obtain all user, consent, and transaction data it needs to fulfill the signing transaction. The IDP provides the full set of verified person data (according to OpenID for Identity Assurance) to the QTSP that the QTSP in turn uses to create a qualified certificate.
Explanation
This flow utilizes the IDPs capability for API Authorization (scope value, lodging intent, user consent, access tokens, token introspection) and the Identity Service in its incarnation for SPs, where the identity data are provided via the OAuth Token Introspection endpoint. (In OAuth terms, the SP is the resource server to which the IDP, the authorization server, grants access to.)
5.6.2. Example: Account Data Analytics
Prerequisites
An SP offers an API that provides RPs with information derived from a user’s bank account history, such as the employer name.
The scope to request authorization for this API and the corresponding lodging intent resource scheme are known to RPs and IDPs. The SP configuration in the platform contains a definition of the requested service access (AIS) along with service access parameters (account history of 180 days).
5.6.3. Using the Analytical Service
An RP wants to use the analytical service. It first determines the IDP and SP to talk to using the account chooser and service configuration.
The RP then creates a lodging intent resource containing the parameter for the intended transaction with the IDP and initiates an authorization process with the IDP using the scope value identifying the lodging intent resource.
Based on scope value and accompanying lodging intent data, the IDP determines the SP’s identity along with the services this SP wants to access on behalf of the user.
The IDP will authenticate the user.
The IDP will then ask the user to allow the RP to access the analytical service on behalf of the user to ask for her employer name grant access to the account information service to the SP and share transaction data up to 180 days with the SP consent to further documents the SP requires the user to consent to (e.g. terms of service)
If the authorization process succeeded, the IDP provides the RP with an access token.
The RP uses the access token to call the analytical service.
The SP receives the request including this access token and uses the IDP’s OAuth Token Introspection Endpoint to obtain related token data in order to validate the authenticity of the token and the authorization of the RP.
The SP cannot use this token directly to access the AIS since it only authorizes the RP to access the SP and is bound to the RP’s TLS client certificate. But the user also authorized access of the SP to the AIS on behalf of the user. The SP therefore uses the token exchange grant type to exchange this access token for an access token minted for the SP’s purposes and TLS Client certificate.
Using this access token, the SP calls the AIS Service of the IDP and obtains transaction data of the last 180 days. It determines the employer of the user based on the salary transactions and responds with this data to the RP.
5.6.4. Explanation
This flow utilizes the IDPs capability for API Authorization (scope value, lodging intent, user consent, access tokens, token introspection) including the ability to exchange tokens issued to a certain client for calling a set of services for another access tokens issued to the SP as client that can be used to call another set of services. Such tokens in turn are used to call the core service for Account Information.
6. Processes
This chapters describes the interactions of the building blocks in the context of relevant processes.
6.1. Partner Onboarding and Management
partners sign up with a Agent and provide their data that is required to act as a legal entity towards .
IDPs can connect their systems to the sandbox system to test their platform integration and utilize the Test RP implementation for testing purpose.
RPs can connect to the sandbox system to test their implementation and to utilize the Test IDP implementation for tests.
6.2. Discover new RPs and SPs
Every IDP needs to know all RPs and SPs including their associated metadata, e.g. the redirect URIs and certificates. This is a prerequisite to serve these RPs in an OAuth or OpenID Connect flow.
It is assumed that every IDP maintains a local copy of this data for the following reasons:
-
Ease of Implementation: we want to facilitate use of commercial OpenID Connect implementations for implementing IDPs. Most implementations assume full control of the RP data and do not support on-demand provisioning of RPs in the event a request is received at the OP’s authorization endpoint with an unknown client_id. The provisioning mechanism envisioned by can be build on top of existing support for OpenID Connect Dynamic Client Registration, which is available in most commercial products.
-
This ensures loose coupling among the scheme participants. It is assumed that the IDP periodically queries the RP Directory to stay in sync. IDPs are advised to synchronize at least every 24h but at most every 10 minutes. The platform offers the mechanisms to sync the RP data and to keep them in sync. The following figures shows the interaction between an IDP and the platform during RP synchronization.
In the first step, it authenticates with the platform AS in order to obtain an access token valid to query RP data from the RP directory. The client_id and certificate used must be set up in the platform AS as part of the IDP onboarding.
Using this access token, the IDP sends a request to the RP Directory to obtain all RP data. The directory, in case of an successful authorization, responds with a JSON array containing all RPs in the directory.
In the course of synchronizing the RP data from the RP directory with the IDP’s local RP directory, IPDs SHOULD NOT remove pre-existing -managed client ids. They should be retained in order to ensure any data within the IDP related to a certain RP, e.g. persistent user consents, are retained over subsequent synchronization processes.
IDPs may recognize pre-existing RPs based on their universally, unique client_id. IDPs can also maintain -managed client ids along with locally managed id since -managed client ids can be recognized based on their prefix, which is always the identity provider in the production environment.
For details on RP & SP management please consult the Platform Documentation.
6.3. Usage Flow
The actual usage flow is divided into the following steps:
-
Invoke Account Chooser and obtain service configuration
-
OpenID Connect/OAuth based authorization process
-
Service Invocation including (optional) Mediation
From the user’s point of view, the process looks like this:
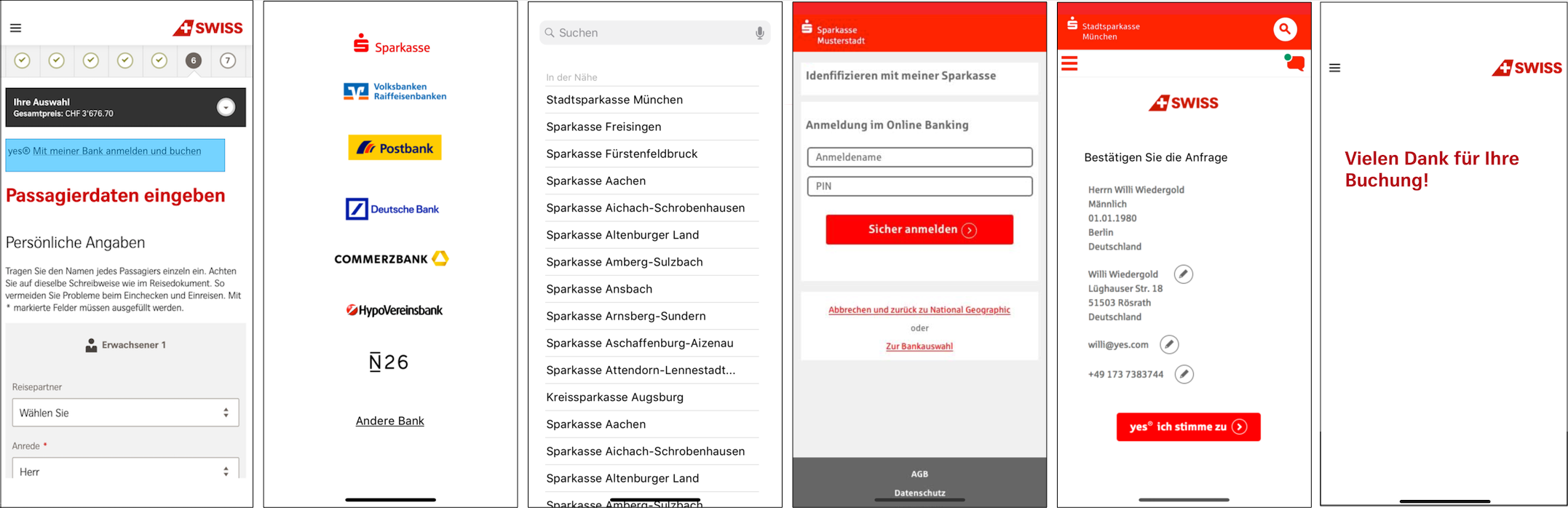
-
The user clicks the button (in this example “Mit meiner Bank anmelden und buchen”) on the RP website or app to identify herself with her online banking credentials.
-
The user agent displays the Account Chooser and prompts the user to select her bank. This is necessary only once per device (or once per iCloud account on Apple devices). As the bank is chosen on accounts.openbanking.verimi.de, the cookie works for any RP. This enables SSO across RPs.
-
The IDP shows the login dialog, where the user enters her banking credentials and hits the login button.
-
The IDP displays a user consent dialog asking for the user’s approval for this particular transaction.
-
After granting access, the user agent displays the RP again. The RP is now able to query the user’s data via the IDP from the core banking system or invoke other services and customize its user experience accordingly. When the RP queries the user data, the IDP invokes the Billing Mediation interface to record the delivery of user and/or account data to the respective RP.
6.3.1. Invoke Account Chooser and Obtain Service Configuration
The process starts when the user clicks on the button at the RP’s website or app. The following figure shows a simplified flow of the bank selection phase (e.g. without error cases).
The RP starts a web flow in the user’s browser (or a
custom tab in case of an app) and invokes the Account
Chooser URL with the its client_id.
Depending on the cookie status and additional parameters, the user is either prompted to choose his bank in the UI of the Account Chooser or the bank is automatically determined based on the cookie settings.
At the end of the user interaction the Account Chooser redirects the browser to the URI configured for the particular RP in the platform and adds the issuer URL of the selected IDP to this redirect URI.
The RP obtains the service configuration by sending the issuer URL to the Service Configuration Service.
The service configuration contains the endpoints and configuration data relevant for the different services provided by the bank IDP. Depending on the service the RP wants to use, different configuration elements are relevant for it.
In any case, the location of the bank IDP metadata is
determined by obtaining the iss element from
the service configuration. The metadata is used to
determine the endpoints for performing the OAuth
authorization process.
If the RP wants to conduct an OpenID Connect process, it uses the same source to determine the location of the OpenID Connect User Info and further data, e.g. supported signing algorithms and the location of the OP’s public keys.
If the RP uses an OpenID Connect library, initializing the library with the issuer URL should be sufficient to kick the process off.
6.3.2. Authorization Process
To start the authorization process, the RP invokes the AS’s authorization endpoint via the user’s browser. The process is sketched out in the following figure.
The RP first discovers the AS’s authorization and token endpoints by utilizing the issuer URL from the service configuration (see above).
It then sends an OAuth authorization request to the AS.
The authorization request contains the regular OAuth
parameters. The scope parameter value depends on the
services and transactions the RP wants to obtain
authorization for. If the authorization request is an
OpenID Connect authentication request, the RP also
includes the claims parameter to specify the
desired user claims and further OpenID Connect request
parameters.
See Developer Guide for a comprehensive documentation of the available scope and claim values.
First, the AS checks whether the client_id is
valid and the redirect_uri exactly matches
one of the redirect URIs defined for this client_id. It
also checks whether the RP is obliged to request the
particular scope and claims values.
Next, the AS authenticates the user. It then displays the services the RP wants to access on behalf of the user and the user data the RP wants to obtain. Depending on the criticality of the services the RP wants to access and the authentication level the RP desired, in case of OpenID Connect, the AS also asks the user to authorize the transaction using her Online Banking TAN method.
If the authorization process succeeded, the AS prepares an
authorization code and sends the user agent back to the RP
using the redirect_uri specified in the
authorization request.
The RP exchanges the authorization code at the AS’s token
endpoint for an access token. This request is mutually
authenticated, where the RP uses the private key
corresponding to one of its certificates configured with
the platform for its client_id. The AS issues
the access token, which is bound the certificate used for
TLS Client Authentication by the RP.
If the request was an OpenID Connect authentication request, the AS (now in its role as OP) also issues an ID Token.
6.3.3. Service Usage (including Mediation)
The implementation of this step depends on the service or services the RP uses.
The following diagram shows the message flow corresponding to the example user flow given above, where the RP uses for obtaining verified identity data.
The RP uses the access token obtained in the authorization process to invoke the OpenID Connect User Info service. The user info service first validates the validity of the access token and what claims are associated with the access token. It then utilizes internal bank services to get the desired data.
Before the User Info service responds to the RP, it creates a record with the Mediation Service. The User Info service first obtains an access token from the Platform AS, which entitles it to create mediation records and subsequently uses it in the call to the Mediation Service. This new record contains data about the service provider that delivered the service, the service type (user info, payment initiation, …) and the delivery time. This data is later collected by the Clearing Service and used to settle and create credits to service providers and invoices for RPs.
The User Info then responds to the RP with the desired user information.
6.3.4. Billing
uses the billing mediation records to produce invoices and credits for RPs and SPs/IDPs, respectively.
In cases where the RP and the IDP involved in a transaction participate in based on a contract with the same Agent, this Agent may opt to perform the billing with these parties itself. This is designated as "on us business".
In this case, will provide the Agent with all billing mediation data and won’t consider the respective transaction(s) in its invoices and credits.
7. References
-
Platform API Documentation, https://docs.sandbox.openbanking.verimi.cloud/
-
The OAuth 2.0 Authorization Framework, https://tools.ietf.org/html/rfc6749
-
The OAuth 2.0 Authorization Framework: Bearer Token Usage, https://tools.ietf.org/html/rfc6750
-
OpenID Connect Core 1.0 incorporating errata set 1, https://openid.net/specs/openid-connect-core-1_0.html
-
OpenID Connect Discovery 1.0 incorporating errata set 1, https://openid.net/specs/openid-connect-discovery-1_0.html
-
NextGenPSD2 XS2A Framework, Implementation Guidelines, https://www.berlin-group.org/nextgenpsd2-downloads
-
PSD 2, https://ec.europa.eu/info/law/payment-services-psd-2-directive-eu-2015-2366_en
-
EBA PSD 2 RTS, http://ec.europa.eu/finance/docs/level-2-measures/psd2-rts-2017-7782_en.pdf
-
eIDAS, https://eur-lex.europa.eu/legal-content/EN/TXT/?qid=1536308959866&uri=CELEX:32014R0910
8. Document History
| Date | Author | Log |
|---|---|---|
|
Jan, 16th 2018 |
Sylwester Kras |
Initial version based on “Gesamtarchitektur ” 0.4 from T. Lodderstedt and further sources. |
|
Jan, 18th 2018 |
Sylwester Kras |
Refinement and 1st runtime aspects |
|
Jan, 25th 2018 |
Sylwester Kras |
Added Feedback from Daniel K. and Torsten L. Improved document and provided sequence diagrams. |
|
Jan, 28th 2018 |
Torsten Lodderstedt |
Document review, reworked introduction and base concept |
|
Feb, 16th 2018 |
Torsten Lodderstedt |
updated logo, modified examples |
|
March, 22th 2018 |
Torsten Lodderstedt |
Incorporated review feedback, modified flow picture |
|
June, 22th 2018 |
Torsten Lodderstedt |
Updated Architecture Diagram, Changed Service Provider to Independent Service Provider |
|
Sept, 10th 2018 |
Torsten Lodderstedt |
Adapted architecture to acquirer model & service discovery, updated IDP-provided services, updated all sequence diagrams, added references |
|
Sept, 12th 2018 |
Torsten Lodderstedt |
Minor editorial changes |
|
Sept, 25th 2018 |
Günter Eder |
Visual Redesign |
|
Oct, 11th 2018 |
Torsten Lodderstedt |
Restructured System Context and Building Blocks Sections |
|
Oct, 29th 2018 |
Torsten Lodderstedt |
Changed Sequence Diagrams to new color scheme |
|
May, 29th 2019 |
Torsten Lodderstedt |
revised document to incorporate the service architecture as well as updates regarding lifecycle management and billing |